
Newly discovered side-channel attack side steps current defense mechanisms
By Ryan Noone
Data compression has long been a technique employed to enhance web performance and the user experience. The process reduces the size of files and resources, such as images, video, and text, before they are transmitted over the internet, significantly reducing the amount of data being transferred and offering faster load times. However, over the years, data compression has become a well-known source of side-channel attacks, capable of leaking users’ personal information to potential adversaries.
In most previously known side-channel attacks, data leaks occur because of software-visible uses of compression. But in a recent study, co-authored by Carnegie Mellon Software and Societal Systems Assistant Professor Riccardo Paccagnella, he and fellow researchers have uncovered a new type of side-channel attack, dubbed GPU.zip, which exploits software-transparent uses of compression. With this unique approach, GPU.zip side steps current side-channel attack defense mechanisms.
“If a user visits a malicious website, GPU.zip enables adversaries to extract pixels from iframes within the site,” said Paccagnella. “Once the attack is finished, the adversary is left with what’s essentially a screenshot of the content rendered within the target iframe.”
In their paper, ‘GPU.zip: On the Side-Channel Implications of Hardware-Based Graphical Data Compression,” the researchers share a proof-of-concept for a realistic attack by “stealing” a username from Wikipedia. The figure below shows the results of their attack on an Intel i7-8700 and an AMD Ryzen 7 4800U. Although their attack was unoptimized, it was completed in just 30 minutes on the AMD Ryzen with 97 percent accuracy. The Intel i7 attack was significantly slower, taking 215 minutes, but saw an accuracy rate of 98.3 percent.
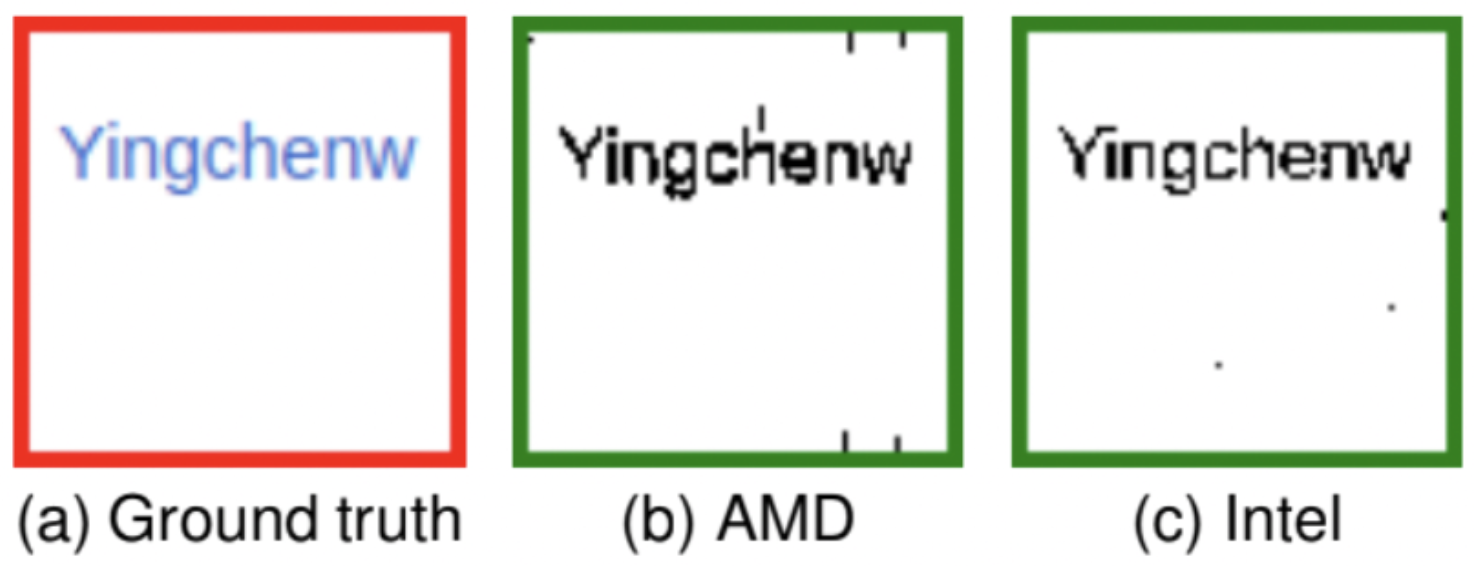
Results of researchers proof of concept attack using GPU.zip. Figure A shows the ground truth, or the way the information was displayed on Wikipedia. Figures B and C show the results of the pixel-stealing attack on an AMD Ryzen 7 and Intel i7.
Researchers say that developers can combat the potential GPU.zip attack by configuring websites to deny being embedded by cross-origin websites and offer a link to a guide on how to do so.
Paccagnella says most websites already deny being embedded by cross-origin websites, relinquishing concern as these sites are not vulnerable to the pixel-stealing attack mounted using GPU.zip. However, users should be aware of which websites they are logged into when navigating to less secure sites on the web.
Researchers disclosed their findings and proof-of-concept code to graphics processing unit (GPU) vendors and Google in March 2023. Up until this point, none of the companies have devised a plan for or committed to patching their products.
When it comes to web browsers, the study’s authors say Google Chrome is vulnerable to pixel-stealing attacks, as it satisfies the following criteria:
- Allows cross-origin iframes to be loaded with cookies
- Allows rendering SVG filters on iframes
- Delegates rendering tasks to the GPU
Other browsers, such as Firefox and Safari, do not meet all the above criteria, thus they are not vulnerable to GPU.zip attacks.
To learn more about GPU.zip, visit https://www.hertzbleed.com/
Paper reference:
GPU.zip: On the Side Channel Implications of Hardware-Based Graphical Data Compression
*To be presented at the 45th IEEE Symposium on Security and Privacy in May 2024
- Yingchen Wang
University of Texas at Austin - Riccardo Paccagnella
Carnegie Mellon University - Zhao Gang
University of Texas at Austin - Willy R. Vasquez
University of Texas at Austin - David Kohlbrenner
University of Washington - Hovav Shacham
Unversity of Texas at Austin - Christopher W. Fletcher
University of Illinois Urbana-Champaign